The Hitchhiker’s Guide to Ransomware: What Ransomware is, How it Works & Ways to Stop it.
Happy July everyone! Wow! Year is definitely flying by. I’ve been asked by many my overall thoughts / plan of action against ransomware, and here it is: Your official (User-friendly!) guide to understanding and preventing ransomware.
You know, a couple of years ago the state of the PC security industry met a remarkable peak: Things were going well security wise. Edge firewalls were getting decent, client PCs finally became stable software / support wise, and operating systems were finally getting remarkably easy to configure / deploy. Windows 7 was the heartbeat of small business, and, for a little bit, the infections of activeX / browser toolbars / fake antivirus seemed to have disappeared. The biggest threat on our list was all those fake search engines / browser manipulators that redirected our searches and landing pages. It seemed (At least for a little bit) that we were able to take a quick breather and finally relax for a few days.
That is, until this beast of an industry came to be:
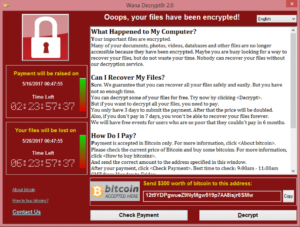
Ah yes, here it is: ransomware. The best (and worst) thing to happen to our industry since Panda antivirus and Windows (Vista) Defender.
But wait, you said “Best” – but ransomware is horrible!
Yes, ransomware is horrible, but, for the first time in a long time – businesses and consumers are beginning to care about their networks, and for sake of argument, their backups.
Before I go any further, let me explain how ransomware came to be, why it’s here to stay, how to protect, as well as how I have been tracking ransomware and predicting where it will go next.
Ransomware takes the very best of what keeps us safe in the world – encryption – and uses it against us as consumers and businesses. To help you understand, encryption is what keeps our online world safe. Encryption keeps our purchases on Amazon safe. Encryption keeps our iPhones safe. Encryption even helps us avoid being spied on or manipulated by corporations or governments. Despite what big media or government says, encryption is here to stay: without it, all of the privacy and peace of mind we have today would be lost. By scrambling data, encryption ensures that only the trusted parties can review the sensitive data that runs our lives. The most common form of encryption today (That we all see) lies right in our web browser.
To make this easy to understand, I won’t go into the specifics on how encryption works, as I may lose you halfway into explaining it, but, if you’re curious, go here.
Basically, at the end of the day, ransomware uses encryption to scramble your PC’s data, and the only way to decode that data is to obtain the unlock key from the hackers (Typically what is referred to as the “private key”). With the introduction of Bitcoin, demanding payment for this key is simple, fast, and *mostly* anonymous. To blame Bitcoin for ransomware, however, is misleading, as many ransomware variants in the past used prepaid money cards or transaction services like Western Union.
Why ransomware is here to stay:
Antivirus is useless
Yup, I said it. In 2017 Antivirus is useless.
To recap for those who don’t know (And that’s ok!) Antivirus is only effective if there is a signature created. What a signature is, is a fingerprint of a known bad, AKA, a virus, worm, or Trojan. That fingerprint / signature is added to a database, where you (Client PCs) are updated to reject these known bads. With ransomware, new variants spread across the internet at rates we never thought were possible. These variants, all have different signatures – making it very hard to identify, reject, and patch systems quickly.
Are we doomed?
Short answer: No.
Longer answer: No – But, we need to be ready. And the time is now.
Since ransomware has a high evasion rate, has a tendency to attack laterally, (meaning jump from computer-computer on a network), and the ability to hold what is most important to you or your business (Files, databases, QuickBooks data, pictures, etc.) it is no secret that ransomware is here to stay as ransomware makes the money. Ransomware is already a billion dollar business.
Ok, so how do we protect against ransomware? To save you time and frustration (money), there is no single silver bullet. The only way to protect against ransomware is a series of solutions / policies put in place to defer ransomware / prevent it. Ultimately, the best approach is to ask yourself, “If I lost everything in my organization / home today, what would I need most” – Chances are, you do not need to backup Windows, or your copy of Microsoft Office, Quickbooks, etc. – As all these products can be easily obtained. What you do care about is your documents, photos, Quickbooks database – Items like these. Follow the industry standard of 3, 2, 1 – 3 backups, 2 onsite, 1 offsite – It’s a great rule of thumb that I believe is here to stay.
Patching / keeping your machines up to date is another important cornerstone. Many of the latest ransomware variants like WannaCry and Petya, use an old attack vector that was patched way back in March of this year. Keep your systems patched! Do not disable updates!
Want to outsmart ransomware? Want to see where it will go next? Look at the patterns.
For all the products in the market today, none (but ours) actually take into account the most common ways ransomware enters a network. If your computer was locked away in a closet, and not connected to the internet, ransomware is not just going to enter by osmosis. An extreme way to look at the situation – but yes, ransomware needs a way to enter the building. So how does it do it?
Ransomware needs a defined intrusion vector and an effective method of growing laterally (From PC-PC).
Common ways include:
- Macros – these pesky little buggers from the 90’s. For system administrators, turn these guys off. I know some of you accountants out there use these macros in Excel and Word.
- Windows scripting host (wscript.exe) – congrats it’s 2017 – move on – disable and reject Windows scripting host. This will effectively eliminate VBscripts from running, which ransomware loves to utilize.
- Reject executables from running inside of Appdata (Local, Roaming, etc.) – Ransomware loves to nestle into this hive of files. Appdata is like the sandbox of Windows. Lots of files live here for temporary reasons. 90% of ransomware uses this area as its nesting ground.
- Disable access to Powershell for end users. Do you ever see an end user use Powershell? Neither do I – and newer ransomware is starting to take advantage of this. Disable.
- SMB1 – Disable it. Already been exploited. Turn it off.
- Disable administrator rights for users. Yes, it’s convenient to be able to install a program without that annoying UAC popup – but ransomware can also run / execute as it needs to with full privileges
- Make sure your drive shares / mapped drives (These little guys)
Are setup correctly in terms of permissions / sharing. If the drive is wide open, meaning anyone can access / modify files – ransomware will look for these drives and encrypt them too.
- Oh, and for you users that use Dropbox: Ransomware like Locky can jump to these too. Best to remove Dropbox from your file / folder windows on as many PCs as you can.
- RDP – Remote desktop – Go ahead and change the RDP port away from 3389 – stumps ransomware creators as they would have to consider every random port, like 5505, to attack via RDP – and it’s not worth their time.
- VSSADMIN- Volume shadow service – that great little service that provides system restore / previous versions – ransomware loves to dive in and delete all copies of your automatic restore points. Go ahead and rename that service – and if you do get infected, your restore points will still be safe (in most cases)
Now that we know the common ways how ransomware enters, how does it make your day even worse? Let’s say for example, you have 15 PCs on a network, and one isn’t patched correctly – well, that one PC can actually be used as a host / bot, and ransomware (in most cases) will have a field day and look for as many mapped drives (shown above) or attached media sources to encrypt. I have seen it in the field before jump to Dropbox, Onedrive, attached USB devices, etc. So, that one Windows XP box in the corner can take out your entire shared drive for your business. Just nice, isn’t it?
A network that is private from the rest of the world is a great method of protection for your offsite backups, remember this.
When a ransomware infection strikes a local network, 9.9/10 times that infection is contained within the local network and cannot jump outside your network. That being said, if your data / backups are also outside your network and are not directly accessible (Whether VPN or directly accessible from a client PC – like a shared drive) your data will physically be safe, and the infection would be contained. For example, if you’re using our Awesomebox backup suite, and your network gets hit with ransomware, your backups would be safe. Why? Because our software uses a series of security measures and filtering to ensure your data is not just one “hop” away – what we mean by this is our client suite acts as a buffer, keeping ransomware from ever touching your backups. Your data is physically disconnected from your network, keeping that pesky little ransomware infection away!
Ransomware will cause us to run to the cloud – but do it cautiously.
Just because your data is in the cloud, does not make it immune to ransomware. The same infrastructure that powers your business also powers the cloud. Always make sure you have another copy of your cloud data secured safely on premise, as well as off premise. I was lucky enough to spend the last 11 months learning / training with the best from Microsoft, IBM, and other big names, as well as incredible professors to understand the momentum of ransomware and how we need to work together to stop it. Now, your local IT manager / company will ultimately need to read this guide, understand the risks / attack points, and lock systems down as much as we can to avoid being disrupted by ransomware.
As these attacks progress into our networks, my prediction for 2017 and on will be:
- More widespread attacks on Macs, Chromebooks, and offsite datacenters such as AWS and Azure.
- Ransomware 2.0 – which will take your data and expose customer info, credit card data, and other sensitive data to the public if demands are not met.
- More lateral attacks on software, such as targeted attacks on QuickBooks, etc.
- More evasion methods like encrypted emails to evade firewalls.
What you should do as a business or a consumer:
Ask yourself
- Do I have a consistent, secured backup solution in house that I know works?
- Do I have an offsite backup solution that is easily accessible?
- Am I using good computing practices like user accounts instead of administrator accounts?
- Am I in connection with my local IT provider to use up to date VPNs, firewalls, security software and good practice procedures?
- Do my employees / family members etc. understand how ransomware is spread / what to look out for?
- If I lost all my data to ransomware today, how fast can we get back up and running?
Dumping all your data in something like Dropbox is one way to go, but how do we place data in these offsite locations, knowing that no one else will be snooping through our files? Use encryption! By encrypting your important files, whether QuickBooks data or your dog’s pictures, you ensure that hackers cannot steal your important data. Let’s go on the offense and use encryption to our advantage. For those customers that use our Awesomebox suite, getting your important data to the cloud – securely – has never been easier. Awesomebox automatically encrypts your files before they are placed onto Dropbox, so you (and only you) can have access to your files. Not us, not Dropbox, not the hackers.
On the settings page, scroll down to the backup and restore section of Awesomebox.
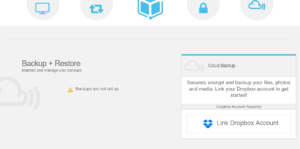
Link your Dropbox account
Once linked, you’ll be placed onto the Backup + Restore page. From here, pick a time, how many copies you wish to keep, and what files / folders are important to you.
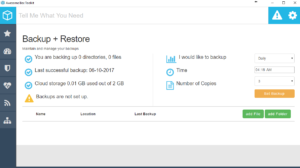
That’s it.
Having an offsite backup is priority #1 Understanding where all your backups are and quickly restoring from them is priority #2. For those who have a RAID array in your servers: I have been asked before, and, no – That is not a backup.
For the extremist:
For the ones who understand Windows networking and wish to lock things down to the max:
- Take all of your Office programs: Word, Excel, Outlook etc. – And place them on a separate virtual machine. Use a new RDP port (Like 5505), and run each app as a remote app in a separate user context. One that does not have access to file / folder shares, mapped drives, etc. This will prevent ransomware from hopping out of the Office programs and onto the network. Neat, right?
- Crack out your batch skills and make some cron jobs. No, not for backups, but to shut down at least one of your backup mediums nightly. Nothing sucks more than waking up to ransomware, only to find out that your one cold storage option was hit too. Backup your data, then safely shut that NAS, SAN, or device down. Ransomware cannot strike if the device is off!
- On a domain? Migrate to folder redirection. Run a virtual machine that holds all your files, then use Powershell the export that VM nightly to your cold storage. Now, you’ll have a copy off all your data in one place, that can easily be restored and placed back into production easily with all of your businesses’ data.
- Mapped drives: Do not map those drives on your servers for backups. Hardcode your backups to use an IP address and ditch those mapped drives, for the reasons stated earlier in this guide.
The best protection is to have a solid, understandable backup plan. Ransomware is deferrable, and having the right backups is the best way to protect yourself, your business, and your assets. For sake of keeping this the most constructive guide on the internet, this Hitchhiker’s Guide to Ransomware will be updated as we see fit. If this guide helped your or your business at all, be sure to share it with your friends. If you’re really happy and want to see me smile, sign up for our software: The Awesomebox Toolkit. In this toolkit you’ll receive ransomware protections (As shown above!) and a solid backup suite that is easy to use – awesome, right?
And remember, never pay the ransom!
Wanna stop #Ransomware? The only cure is to stop it from happening in the first place. Yes, it's really this simple #Oneclick #Awesomebox pic.twitter.com/o4SqM4sHtu
— Awesomebox Tech (@awesomeboxtech) May 19, 2017